It came up recently that I needed to capture traffic from a remote router interface to troubleshoot some SIP issues. The easy option is to create a mirrored port and plug in directly to capture the traffic locally. But I didn't have the luxury of a spare port. Instead, I utilized a GRE tunnel to send IP traffic from the remote location to a VM in my datacenter. Here's how I did it.
Overview
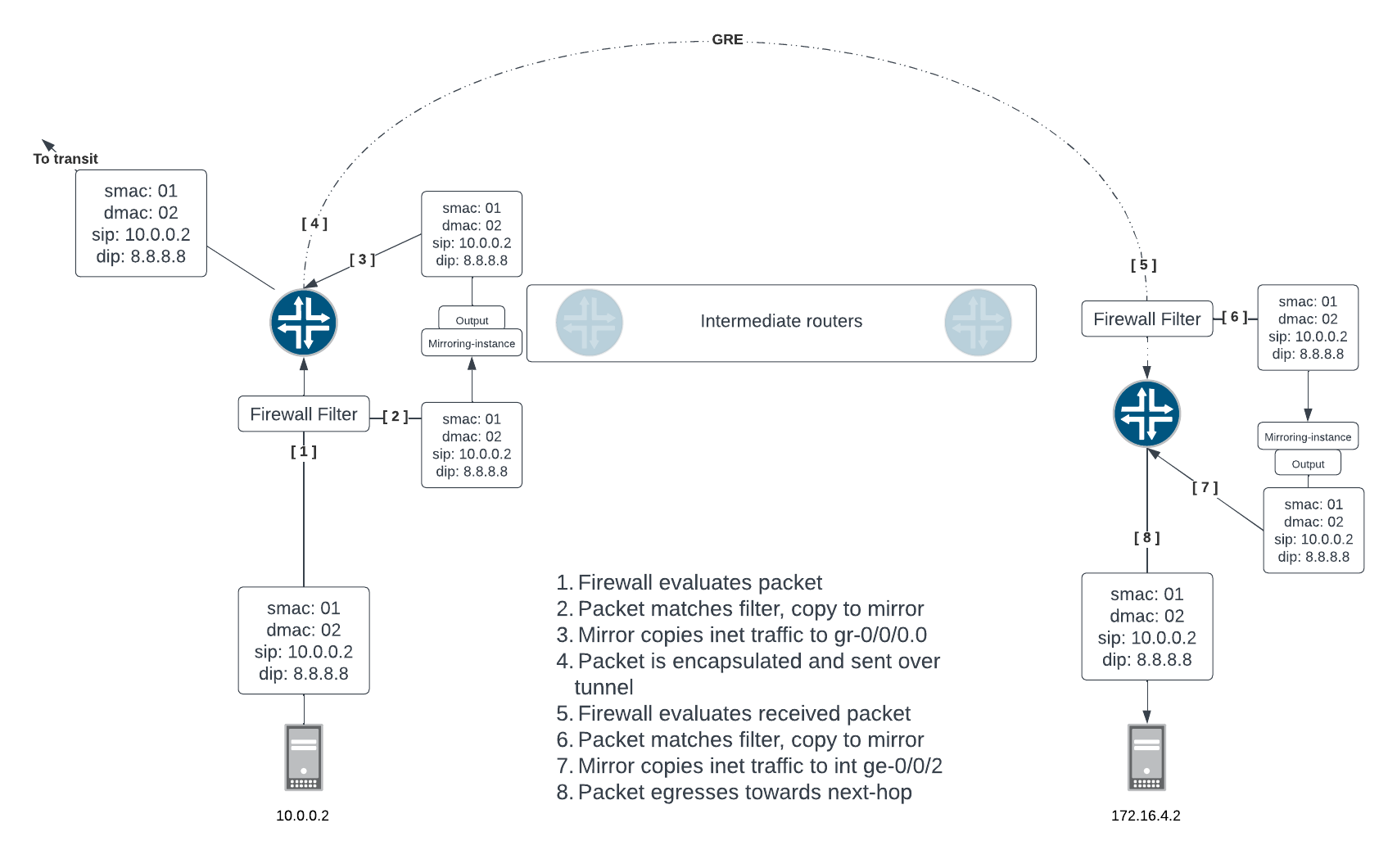
Simplified Topology
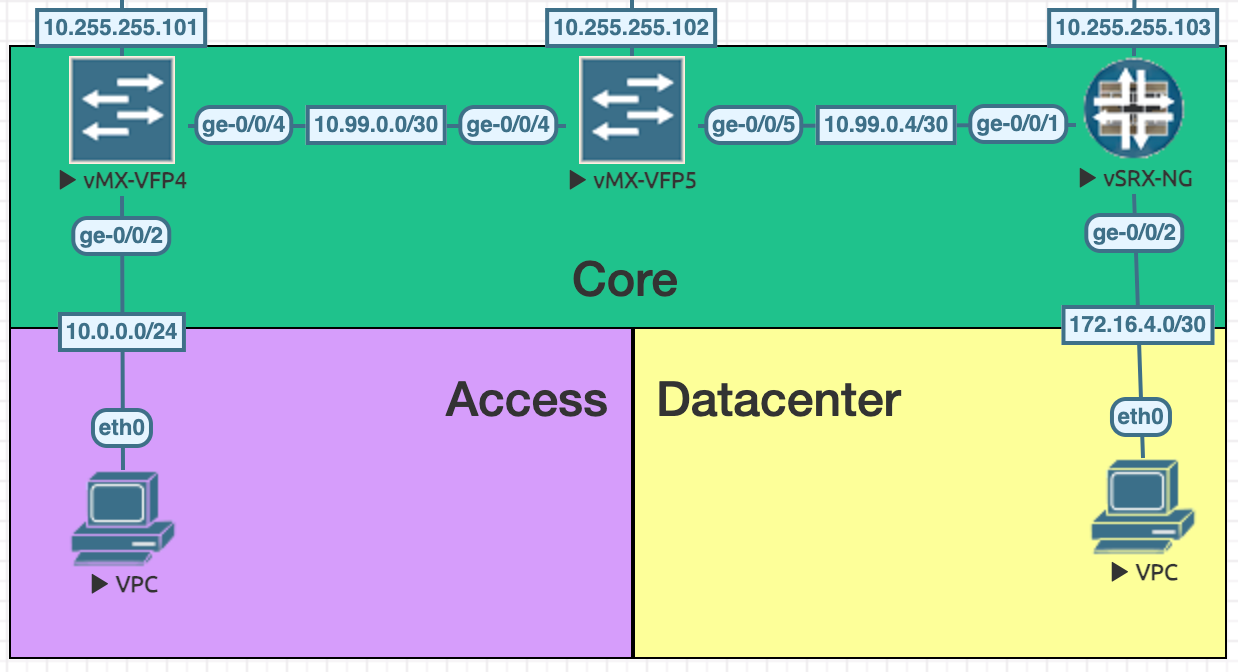
For simplicity sakes, I only have a single transit router, in reality, this connection would likely be over many routers and even over the internet (bad idea).
In the access side, we have a single PC connected to the 10.0.0.0/24 network with 10.0.0.1/24 as the gateway interface on VFP4 ge-0/0/2.
Goal: I'd like to know if specific tx/rx traffic from a specific customer is reaching the core.
Plan: Create a firewall rule to match specific traffic, when matched, uplift the traffic into a port mirror instance. The port mirror instance will output the mirror packets to a GRE tunnel. The other end of the GRE tunnel will be your linux server, but in the lab case, simply another router. Finally, we will create another firewall and port mirror to copy packets out of the GRE tunnel and onto a local port.
Capture Side
Creating the firewall filter
set firewall family inet filter copy-dataplane term mirror-packets from source-address 10.0.0.2/32
set firewall family inet filter copy-dataplane term mirror-packets then port-mirror-instance pcap-server
set firewall family inet filter copy-dataplane term accept then accept
firewall {
family inet {
filter copy-dataplane {
term mirror-packets {
from {
source-address {
10.0.0.2/32;
}
}
then count packet_hits
then port-mirror-instance pcap-server;
}
term accept {
then accept;
}
}
}
}Applying the firewall filter
set interfaces ge-0/0/2 unit 0 family inet filter input copy-dataplane
set interfaces ge-0/0/2 unit 0 family inet filter output copy-dataplane
set interfaces ge-0/0/2 unit 0 family inet address 10.0.0.1/24interfaces {
ge-0/0/2 {
unit 0 {
family inet {
filter {
input copy-dataplane;
output copy-dataplane;
}
address 10.0.0.1/24;
}
}
}
}Creating the Port Mirror
set chassis fpc 0 pic 0 tunnel-services
set chassis fpc 0 port-mirror-instance pcap-server
set forwarding-options port-mirroring instance pcap-server input rate 1
set forwarding-options port-mirroring instance pcap-server input run-length 1
set forwarding-options port-mirroring instance pcap-server family inet output interface gr-0/0/0.0chassis {
fpc 0 {
pic 0 {
tunnel-services;
}
port-mirror-instance pcap-server;
}
}forwarding-options {
port-mirroring {
instance {
pcap-server {
input {
rate 1;
run-length 1;
}
family inet {
output {
interface gr-0/0/0.0;
}
}
}
}
}
}Creating the GRE Tunnel
set interfaces gr-0/0/0 unit 0 description "MIRROR: PCAP SERVER"
set interfaces gr-0/0/0 unit 0 tunnel source 10.255.255.101
set interfaces gr-0/0/0 unit 0 tunnel destination 10.255.255.103
set interfaces gr-0/0/0 unit 0 family inet address 10.100.200.1/30interfaces {
gr-0/0/0 {
unit 0 {
description "MIRROR: PCAP SERVER";
tunnel {
source 10.255.255.101;
destination 10.255.255.103;
}
family inet {
address 10.100.200.1/30;
}
}
}
}Mirror side (Linux Option)
It is simpler to GRE tunnel straight to a linux server that can run the tcpdump.
sudo modprobe ip_gre
sudo ip tunnel add gre1 mode gre remote 10.255.255.101 local 172.16.4.2 ttl 255
sudo ip link set gre1 up
sudo ip addr add 10.0.0.2/30 dev gre1
sudo tcpdump -i gre1Mirror side (Router Option)
Creating the firewall filter
set firewall family inet filter copy-dataplane term all then count packet_hits
set firewall family inet filter copy-dataplane term all then port-mirror-instance pcap-server
set firewall family inet filter copy-dataplane term accept then acceptCreating the GRE tunnel and applying the firewall filter
set interfaces gr-0/0/0 unit 0 tunnel source 10.255.255.103
set interfaces gr-0/0/0 unit 0 tunnel destination 10.255.255.101
set interfaces gr-0/0/0 unit 0 family inet filter input copy-dataplane
set interfaces gr-0/0/0 unit 0 family inet address 10.100.200.2/30interfaces {
gr-0/0/0 {
unit 0 {
tunnel {
source 10.255.255.103;
destination 10.255.255.101;
}
family inet {
filter {
input copy-dataplane;
}
address 10.100.200.2/30;
}
}
}
}Creating the Port Mirror
set forwarding-options port-mirroring input rate 1
set forwarding-options port-mirroring input run-length 1
set forwarding-options port-mirroring family inet output interface ge-0/0/2.0 next-hop 172.16.4.2forwarding-options {
port-mirroring {
input {
rate 1;
run-length 1;
}
family inet {
output {
interface ge-0/0/2.0 {
next-hop 172.16.4.2;
}
}
}
}
}Validation
Checking the state of each component
- Check interface counters of the interface you are looking to capture
- Check the firewall filter hit counter to make sure you are matching packets
- Check the state of the GRE tunnel
- Check the state of the port-mirror
1. show interface ge-0/0/2 | match pps
2. show firewall counter packet_hits filter copy-dataplane
3. show interface terse gr-0/0/0.0
4. show forwarding-options port-mirroring
Fixing ARP to Fix mirroring (Router Option only)
The router is not going to ARP for the next-hops MAC. If the server is not also being talked to by other devices, your port-mirror will be down. To have the best experience, set a static ARP entry.
set interfaces ge-0/0/2 unit 0 family inet address 172.16.4.1/30 arp 172.16.4.2 mac 00:11:22:33:44:55interfaces {
ge-0/0/2 {
unit 0 {
family inet {
address 172.16.4.1/30 {
arp 172.16.4.2 mac 00:11:22:33:44:55;
}
}
}
}
}

